¡HI! If you want to propose us a project, send a mail to info@albatian.com


ALL INFORMATION ABOUT
BPM, PROCESS, R & D, TECHNOLOGY
The Whole truth about safety
By Bernardo Ramos, IT security expert

Passwords
Today we are going to talk about passwords, that unpleasant thing that we always remember when we want to access some service on the Web, that we have never been stolen, that is very safe and nobody could guess and, besides, even in that case, I would not care because I change it frequently. Because, of course, we all stick to the safety recommendations that we are reading or listening every day. Or maybe not? On the other hand, are these recommendations really justified? What is the real ...
(Keep reading)A strong Enterprise Architecture practice will help prepare organizations for GDPR
By: Pedro Robledo, BPM process management expert
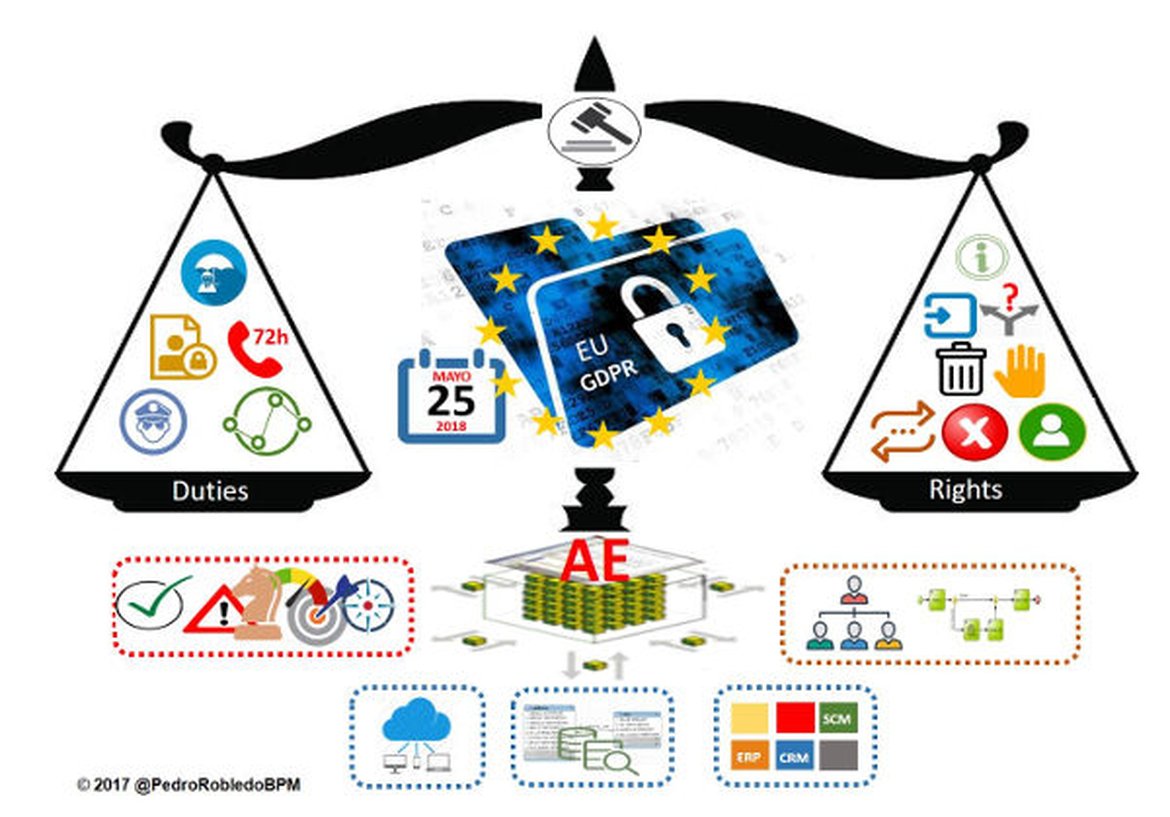
Any private or public organization anywhere in the world could be caught by General Data Protection Regulation (GDPR, EU Regulation 2016/679) if it processes personal data relating to EU citizens, has a European presence, or has a website offering goods or services to EU citizens. And it critically affects all personal data, changing the way that entire organizations interact with personally identifiable information. It requires changes in both security and processing as well as in the comprehensive documentation they must maintain ...
(Keep reading)Industry 4.0: the bpm challenge
By Juan Emilio Alvárez, Specialist in Digital transformation and BPM

"The Industrial Revolution 4.0 and / or Digital Transformation,”, is already a reality. This transformation implies a reinvention, but, unlike previous transformations, times are critical. Supply and demand vary at Vertiginous speed, and every company has to find its way to success. In this scenario, is it possible to bypass digital transformation 4.0?
The immersion in the "Digital Transformation" has to be a reality, but do not confuse Digital Transformation, with change of technology. Elements such as manufacturing and additive intelligence, robotics, artificial ...
(Keep reading)How to Calculate the ROI of a BPM Initiative?
By: Pedro Robledo, BPM process management expert
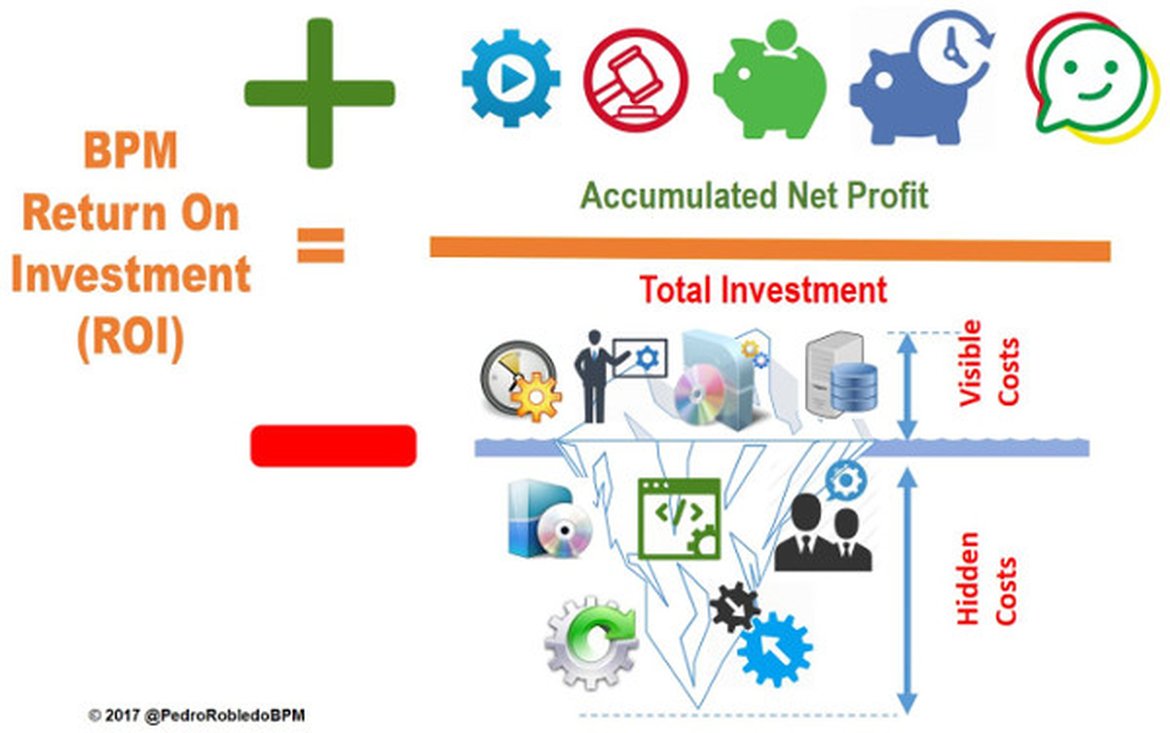
As the implementation of BPM (Business Process Management) in your organization is not only the implementation of BPM technology, to analyze the profitability to be obtained it is necessary to take into account the entire BPM Life Cycle. You must evaluate both the investment to be made and the benefits in each phase. It is also necessary to take into account in the analysis the number of BPM projects that will be implemented during the time period of study so that all costs in ...
(Keep reading)Payback of management misinformed by excess - PCs in the industrial environment
By Bernardo Ramos, IT security expert

A few weeks ago media around the world alarmed citizens with a "Ransomware" attack which they called "Wannacry". It had blocked lots of computers of some major companies around the world
Shortly afterwards the same media again alarmed us with a new wave of even more sophisticated attacks of the same type. Now they explained that Russia had used a cyber weapon called "Petya" to attack Ukraine with possible unpredictable effects in other countries.
Enterprise executives are not usually concerned with issues such ...
(Keep reading)










